Difference between revisions of "Router Info Sonicwall"
(complete sonicwall info revamp) |
|||
| Line 1: | Line 1: | ||
| − | + | ===Disable SIP Header Transformations and Enable Consistent NAT=== | |
| − | + | SonicWALL SIP ALG is called SIP Header Transformations, this should be Disabled and Consistent NAT should be Enabled:<br/> | |
| + | [[File:Sonicwallcnsht.png]] | ||
| − | + | ===Create Outbound NAT Policy and Disable Source Port Remap=== | |
| − | + | In some cases the SonicWALL will remap the 5060 and 10000-20000 UDP source ports causing one way audio and calls dropping after 30 seconds. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | To resolve this, create an inside to outside rule like the following: | |
| + | <table> | ||
| + | <tr> | ||
| + | <td> | ||
| + | '''Original Source:''' <br/> | ||
| + | '''Translated Source:''' <br/> | ||
| + | '''Original Destination:''' <br/> | ||
| + | '''Translated Destination:''' <br/> | ||
| + | '''Original Service:''' <br/> | ||
| + | '''Translated Service:''' <br/> | ||
| + | '''Inbound Interface:''' <br/> | ||
| + | '''Outbound Interface:''' | ||
| + | </td> | ||
| + | <td><div style="margin-left: 30px;"> | ||
| + | PBX Private IP<br/> | ||
| + | IP of the WAN interface (X1 IP for example)<br/> | ||
| + | Address Group for our SIP servers (52.5.220.123 or 54.200.236.200)<br/> | ||
| + | Original<br/> | ||
| + | Service Group including 5060 UDP and 10000-20000 UDP<br/> | ||
| + | Original<br/> | ||
| + | Any<br/> | ||
| + | WAN interface (X1 for example) | ||
| + | </div></td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | After that go to the Advanced tab and check the box for "Disable Source Port Remap" and click OK.<br/> | ||
| + | [[File:Sonicwallspr.PNG]]<br/> | ||
| + | Once completed the PBX will always use the proper source ports on the WAN side. | ||
| + | ===Create Access Policy with Increased UDP Timeout=== | ||
| − | + | Most often seen in cloud deployments you will see phones going REACHABLE/UNREACHABLE with complaints of calls going directly to voicemail and BLFs not lighting properly. | |
| − | + | To fix this add a LAN to WAN Access Policy as follows: | |
| + | <table> | ||
| + | <tr> | ||
| + | <td> | ||
| + | '''From Zone:''' <br/> | ||
| + | '''To Zone:''' <br/> | ||
| + | '''Service:''' <br/> | ||
| + | '''Source:''' <br/> | ||
| + | '''Destination:''' <br/> | ||
| + | '''Users Allowed:''' <br/> | ||
| + | '''Schedule:''' | ||
| + | </td> | ||
| + | <td><div style="margin-left: 30px;"> | ||
| + | LAN<br/> | ||
| + | WAN<br/> | ||
| + | SIP (UDP 5060)<br/> | ||
| + | Any<br/> | ||
| + | Any<br/> | ||
| + | All<br/> | ||
| + | Always On | ||
| + | </div></td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | |||
| + | Navigate to the Advance tab and reduce the UDP timeout to 30 seconds, once saved phones should remain REACHABLE. | ||
Revision as of 18:47, 18 November 2021
Disable SIP Header Transformations and Enable Consistent NAT
SonicWALL SIP ALG is called SIP Header Transformations, this should be Disabled and Consistent NAT should be Enabled:
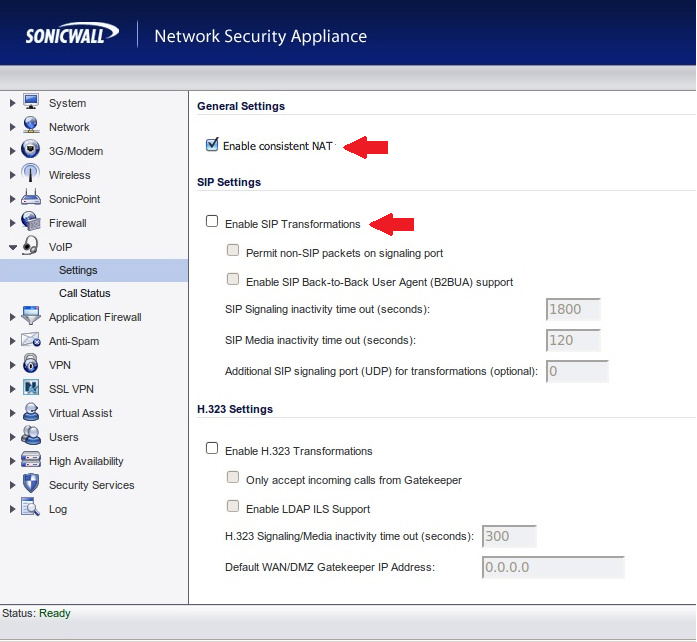
Create Outbound NAT Policy and Disable Source Port Remap
In some cases the SonicWALL will remap the 5060 and 10000-20000 UDP source ports causing one way audio and calls dropping after 30 seconds.
To resolve this, create an inside to outside rule like the following:
|
Original Source: |
PBX Private IP |
After that go to the Advanced tab and check the box for "Disable Source Port Remap" and click OK.
File:Sonicwallspr.PNG
Once completed the PBX will always use the proper source ports on the WAN side.
Create Access Policy with Increased UDP Timeout
Most often seen in cloud deployments you will see phones going REACHABLE/UNREACHABLE with complaints of calls going directly to voicemail and BLFs not lighting properly.
To fix this add a LAN to WAN Access Policy as follows:
|
From Zone: |
LAN |
Navigate to the Advance tab and reduce the UDP timeout to 30 seconds, once saved phones should remain REACHABLE.