Router Info
This page contains general information about port forwarding and disabling application layer gateways on particular routers.
Sonicwall
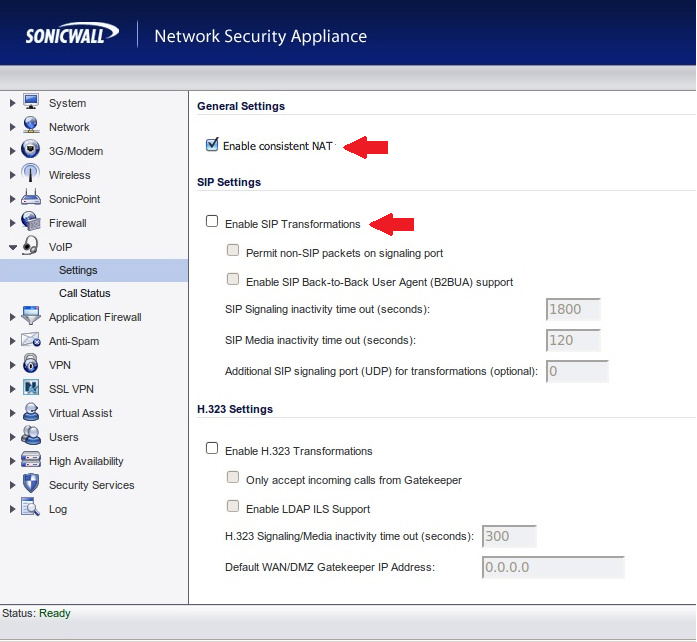
Disable SIP Header Transformations and Enable Consistent NAT
SonicWALL SIP ALG is called SIP Header Transformations, this should be Disabled and Consistent NAT should be Enabled:
Create Outbound NAT Policy and Disable Source Port Remap
In some cases the SonicWALL will remap the 5060 and 10000-20000 UDP source ports causing one way audio and calls dropping after 30 seconds.
To resolve this, create an inside to outside rule like the following:
|
Original Source: |
PBX Private IP |
After that go to the Advanced tab and check the box for "Disable Source Port Remap" and click OK.
File:Sonicwallspr.PNG
Once completed the PBX will always use the proper source ports on the WAN side.
Create Access Policy with Increased UDP Timeout
Most often seen in cloud deployments you will see phones going REACHABLE/UNREACHABLE with complaints of calls going directly to voicemail and BLFs not lighting properly.
To fix this add a LAN to WAN Access Policy as follows:
|
From Zone: |
LAN |
Navigate to the Advance tab and increase the UDP timeout to 300 seconds, once saved phones should remain REACHABLE.
Mikrotik
This router has an ALG that can be disabled with the following command
/ip firewall service-port disable sip
The info was found at the following two links Mikrotik Wiki Mikrotik Forum
Fortigate
I found this online about solving issues with Fortigate routers and NO AUDIO with remote SIP:
In the command line of the fortigate type the following:
config system settingsset sip-helper disableset sip-nat-trace disable
Reboot the device
In the command line type the following:
config system session-helpershow
(now look for SIP, mostly it will be "12")
delete 12
Don't use any protection profiles on the firewall of the sip rules.
Cisco Pix 506/501/515 and Cisco ASA
- access-list 101 permit udp any host 64.238.XXX.XXX range 10000 20000
(Note: Replace 64.238.XXX.XXX with your public IP assigned to be forwarded to the IPitomy PBX) - access-list 101 permit tcp any host 64.238.XXX.XXX range 10000 20000
(Note: Replace 64.238.XXX.XXX with your public IP assigned to be forwarded to the IPitomy PBX) - static (inside,outside) 64.238.XXX.XX 172.16.2.129 netmask 255.255.255.255 0 0
(Note: Replace 64.238.XXX.XXX with users public IP, replace the 172.16.2.129 with users private IP that is assigned to the IPitomy PBX) - no fixup protocol sip 5060
- no fixup protocol sip udp 5060
Adtran
From a recent interaction with an AdTran tech, it was shown to us there is a setting for "proxy transparency" that needs to be enabled in order for all of the SIP traffic to pass unhindered. This was when the Adtran was the routing device at the remote site, but likely would need to be enabled when the Adtran is at the PBX site. Its worth trying for sure.
PepLink
Here is a document sent to a dealer from PepLink regarding configuration settings that may be required for Remote SIP to function properly:
FIOS ActionTec
We have found the following article that outlines some possible configurations that are available on the Actiontec Modem/Router combo that FIOS is installing. This gives some options on ways to configure to optimize VoIP and SIP traffic passing to remote.
http://www.dslreports.com/faq/verizonfios/3.0_Networking#16077
Comcast Modem
We have received some information from our dealers that if your site has a Comcast modem/router, you should request a SMC and not a Linksys, as the reports are that the SMC handles VoIP more consistently. Additionally, there may be issues with Comcast modem/routers ability to handle multiple concurrent NAT sessions, limiting the number of remote phones you can install at a remote site.